A9 Firewall¶
Implementation¶
The PodNet’s Network Firewall is divided into 2 parts, such as:
Main Namespace Firewall
Project Namespace Firewall
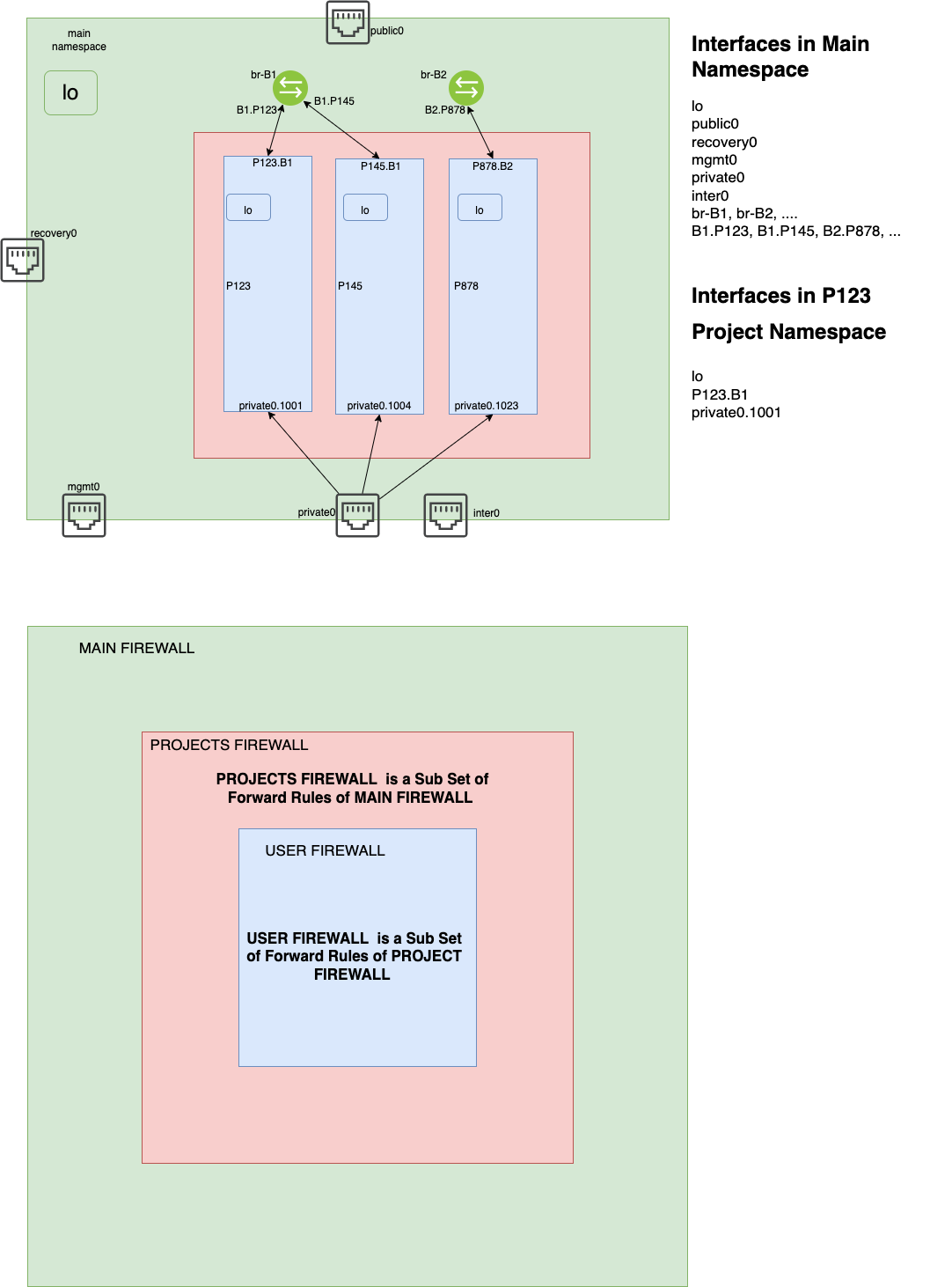
Main Namespace Firewall¶
The Main Namespace Firewall is applied during PodNet Installation. Every PodNet is installed with a default Firewall configuration. The rules of Firewall configuration are based on Network Interfaces defined in the Main Namespace and those are:
lo
public0
mgmt0
oob0
private0
inter0
br-B<subnet_id> …. (all Floating subnet bridge gateway interfaces)
B<subnet_id>.P<project_id> …. (all link terminals connecting from Project to Floating subnet bridges)
The Main Namespace Firewall is divided into 5 sections, those are:
Inbound or Input
Outbound or Output
Forward
Pre-routing
Post-routing
Inbound¶
This section is for set of rules that defines the network traffic destined to the interfaces in Main Namespace ie only entering but not leaving, so only Input interface of the rule is involved.
The default Inbound firewall policy is drop and all accept rules are as follows:
Name |
Input Interface |
Output Interface |
version |
source |
destination |
protocol |
port |
log |
flavor |
|---|---|---|---|---|---|---|---|---|---|
a |
lo |
4 |
|
|
icmp |
True |
pat, cop, region |
||
b |
lo |
4 |
|
|
dns |
True |
pat, cop, region |
||
c |
public0 |
4 |
|
|
icmp |
True |
pat, cop, region |
||
d |
public0 |
4 |
|
|
vpn |
True |
pat, region |
||
e |
mgmt0 |
4 |
|
|
icmp |
True |
pat, cop, region |
||
f |
oob0 |
4 |
|
|
icmp |
True |
pat, cop, region |
||
g |
oob0 |
4 |
|
|
tcp |
22 |
True |
pat, cop, region |
|
h |
lo |
6 |
|
|
icmp6 |
True |
pat, cop, region |
||
i |
public0 |
6 |
|
|
icmp6 |
True |
pat, cop, region |
||
j |
mgmt0 |
6 |
|
|
icmp6 |
True |
pat, cop, region |
||
k |
mgmt0 |
6 |
|
|
tcp |
22 |
True |
pat, region |
oob_ip: PodNet A - 100.64.<pod_number>.254 and PodNet B - 100.64.<pod_number>.253
applinace_ips: <ip6>::6000:1, <ip6>:d0c6::6001:1, <ip6>:doc6::6001:2
pat assignments: public subnet assignments of PAT
<ip6> means first 3 hextets of ipv6_subnet of the Pod, eg `2a02:2078:9`
pms: IPv4 Primary Management subnet
ff00::/8 - is used primarily for Neighbor Discovery Protocol (NDP) on IPv6 networks
Outbound¶
This section is for set of rules that defines the network traffic originated from the interfaces in Main Namespace ie only leaving but not entering, so only Output interface of the rule is involved.
The default Outbound firewall policy is drop and accept rules are as follows:
Name |
Input Interface |
Output Interface |
version |
source |
destination |
protocol |
port |
log |
flavor |
|---|---|---|---|---|---|---|---|---|---|
a |
any |
4 |
|
|
any |
any |
True |
pat, cop, region |
|
b |
any |
6 |
|
|
any |
True |
pat, cop, region |
mgmt_ip PodNet A - <ip6>::10:0:2 and PodNet B - <ip6>::10:0:3
Forward¶
This section is for set of rules that defines the network traffic neither generated from nor destined to the interfaces in Main Namespace but are involved in the traffic flow ie entering and leaving ,so input interface and output interface are involved.
The default Forward firewall policy is drop and accept rules are as follows:
Name |
Input Interface |
Output Interface |
version |
source |
destination |
protocol |
port |
log |
flavor |
|---|---|---|---|---|---|---|---|---|---|
a |
public0 |
mgmt0 |
4 |
|
|
icmp |
True |
pat, cop, region |
|
b |
public0 |
mgmt0 |
4 |
|
|
tcp |
443 |
True |
pat, cop |
c |
mgmt0 |
public0 |
4 |
|
|
any |
True |
pat, cop, region |
|
d |
FWD interfaces* |
FWD interfaces* |
4 |
|
|
any |
True |
pat, region |
|
e |
public0 |
mgmt0 |
6 |
|
|
icmp6 |
True |
pat, cop, region |
|
f |
public0 |
mgmt0 |
6 |
|
|
tcp |
443 |
True |
pat, cop |
g |
mgmt0 |
public0 |
6 |
|
|
any |
True |
pat, cop, region |
|
h |
FWD interfaces* |
FWD interfaces* |
6 |
|
|
any |
True |
pat, region |
FWD interfaces = [public0, br-B<subnet_id>, B<subnet_id>.P<project_id>] or !=[mgmt0, oob0, private0, inter0]
FWD interfaces are also the Interfaces involved in Project Namespace Firewall
Pre-Routing¶
This section is for set of rules to filter out all the traffic just before entering the Main Namespace interfaces
The default Pre-Routing firewall policy is accept and drop rules are as follows:
Name |
Input Interface |
Output Interface |
version |
source |
destination |
protocol |
port |
log |
flavor |
|---|---|---|---|---|---|---|---|---|---|
a |
any |
4 |
|
|
any |
True |
pat, cop, region |
||
b |
any |
6 |
|
|
any |
True |
pat, cop, region |
ipv4/ipv6 RoboSOC Block list from https://www.cloudcix.com/ipblocklist.txt
Post-Routing¶
This section is for set of rules to filter out all the traffic just after leaving the Main Namespace interfaces
The default Pre-Routing firewall policy is accept and drop rules are as follows:
Name |
Input Interface |
Output Interface |
version |
source |
destination |
protocol |
port |
log |
flavor |
|---|---|---|---|---|---|---|---|---|---|
a |
any |
4 |
|
|
any |
True |
pat, cop, region |
||
b |
any |
6 |
|
|
any |
True |
pat, cop, region |
Project Namespace Firewall¶
All the Projects Namespace Firewall is a subset of Main Namespace Firewall. The rules e and j of Forward rules section of Main Namespace Firewall default configuration implies the All the Projects Namespaces Firewall. All the User defined firewall rules within a Project is an instance of NFtables applied within their respective Project’s Namespace. The rules of Firewall configuration are based on Network Interfaces defined in the Project Namespace and those are:
lo
P<project_id>.B<subnet_id> (the link terminal connecting Project Namespace to its gateway’s Floating subnet bridge)
private0.<vlan_number> (the vlan tagged private interface connecting Project Namespace to Private Network Switch)
inter0.<vlan_number> (the vlan tagged inter interface connecting Project Namespace to Inter Network Switch)
xfrm.<stif_number> (the secure tunnel tagged XRFM interface connecting Project Namespace to Main Namespace for VPN termination)
The Project Namespace Firewall is divided into 5 sections, those are:
Inbound or Input
Outbound or Output
Forward
Pre-routing
Post-routing
Inbound¶
This section is for set of rules that defines the network traffic destined to the interfaces in Project Namespace ie only entering but not leaving, so only Input interface of the rule is involved.
The default Inbound firewall policy is drop and no accept rules are defined.
Outbound¶
This section is for set of rules that defines the network traffic originated from the interfaces in Project Namespace ie only leaving but not entering, so only Output interface of the rule is involved.
The default Inbound firewall policy is accept and no drop rules are defined.
Forward¶
This section is for set of rules that defines the network traffic neither generated from nor destined to the interfaces in Project Namespace but are involved in the traffic flow ie both entering and leaving ,so input interface and output interface are involved.
The default Forward firewall policy is drop.
Since the RoboSOC Blocklist is applied at Main Namespace level, it is implicit that RoboSOC blocklist is acting on Project Namespace
All the User defined Inbound and Outbound rules are subset of Project Namespace Forward Firewall.
Both accept and drop rules can be added by the User.
Pre-Routing¶
This section is for set of rules to filter out all the traffic just before entering the Project Namespace interfaces
The default Pre-Routing firewall policy is accept.
All the Destination NAT accept rules are added in this section.
Post-Routing¶
This section is for set of rules to filter out all the traffic just before leaving the Project Namespace interfaces
The default Pre-Routing firewall policy is accept.
All the Source NAT accept rules are added in this section.