PodNet HA¶
Introduction¶
PodNet High Availability (HA) is managed by PAT Commanders via the OOB network and using the “pat” UID account. When PodNets need to be upgraded or replaced this capability allows failover between two PodNets, a Primary (A) and Secondary (B). Command scripts are available to disable a PodNet, being taken out of service, and to enable a PodNet, being put into service. These command scripts are in a directory that is chmod restricted to the “pat” UID account. The enabled/disabled state of the PodNets in a Pod is recorded in the config.json of each PodNet device. The PodNet HA is firewall protected by the Main Firewall.
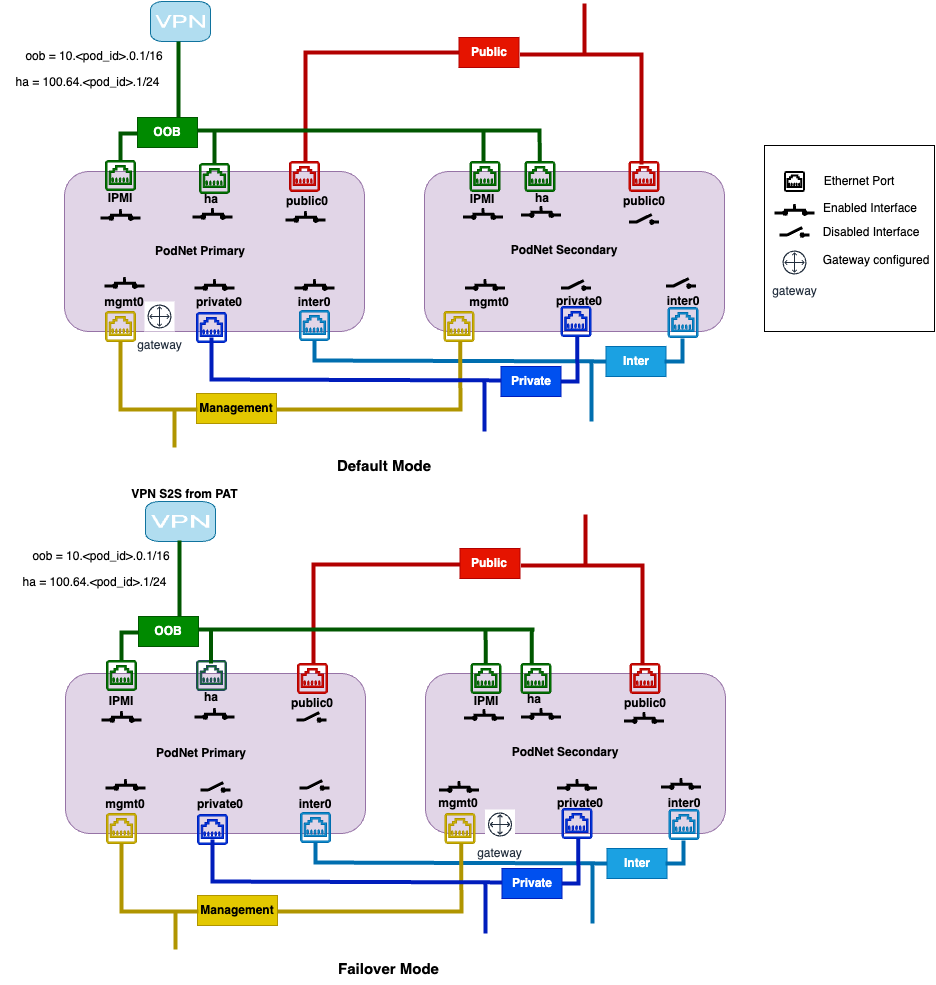
Network Connectivity¶
Public Interface
Both PodNets are equipped with Public interfaces and are always disabled by default.
IPv4: Both PodNet Public interfaces are configured with IPv4_CPE (the 2nd usable IP of a IPv4 link subnet) and IPv4_PE (the 1st usable IP of a IPv4 link subnet) as its Gateway.
IPv6: Both PodNet Public interfaces are configured with IPv6_CPE (the 2nd usable IP of a IPv6 link subnet) and IPv6_PE (the 1st usable IP of a IPv6 link subnet) as its Gateway.
Private Inteface
Both PodNets are equipped with Private interfaces and are always disabled by default.
Both PodNet Private interfaces have no IP addressing.
Management Interface
Both PodNets are equipped with Management interfaces and are always enabled by default.
IPv4: PodNet A Management interface is configured with PMS4+2 (2nd usable IP of IPv4 Primary Management Subnet), while PodNet B Management interface configured with PMS4+3 (the 3rd usable IP of PMS4).
IPv6: PodNet A Management interface is configured with PMS6+2 (2nd usable IP of IPv6 Primary Management Subnet), while PodNet B Management interface configured with PMS6+3 (the 3rd usable IP of PMS6).
Gateway: PMS4+1 (1st usable IP of PMS4) and PMS6+1 (1st usable IP of PMS6) are not configured by default for either of the PodNets.
OOB Interface
Both PodNets are equipped with OOB interfaces and are always enabled by default.
IPv4: PodNet A OOB interface is configured with 10.<pod_number>.0.254/16 while PodNet B configured with 10.<pod_number>.0.253/16 and both have same gateway as 10.<pod_number>.0.1
Disabling a PodNet¶
The disable.sh script, vailable from the PAT, disables the PodNet on which it is run. This command is ran by a PAT engineer.
Steps
- Checks the PodNet is correctly enabled as follows and gives feedback to “pat” UID of unexpected status
Enabled in config.json
Public interface is UP
Private interface is UP
Inter Region interface is UP
Management interface is UP and gateway IP is configured.
PAT commander proceeds or aborts based on feedback above.
Sets the Public and Private interfaces DOWN.
Removes PMS4+1 and PMS6+1 IP addresses from the Management Interface.
Trigger an action to update config.json on the Pod Appliance.
Enabling a PodNet¶
The enable.sh script, available from the PAT enables the PodNet on which it is run. This command is ran by a PAT engineer.
Steps
- Checks the PodNet is disabled as follows and gives feedback to “pat” UID of unexpected status
Disbled in config.json
Public interface is DOWN
Private interface is DOWN
Inter Region interface is DOWN
Management interface is UP and gateway IP is not configured.
PAT commander proceeds or aborts based on feedback above.
Sets the Public and Private interfaces UP.
Adds PMS4+1 and PMS6+1 IP addresses to the Management Interface.
Trigger an action to update config.json on the Pod Appliance.
Main Firewall¶
The Main Firewall is a group of Linux NFTable rules triggered by PAT Commanders and are applied by Robot. The Main Firewall is first applied on the Active PodNet only to allow the Rollback capability in case of firewall misconfiguration by simply disabling the new firewall applied PodNet and enabling the other. When the newly applied Main Firewall is accepted then applied on the Standby PodNet as well.
Conclusion¶
PodNet’s high availability architecture, coupled with dynamic interface management through enable.sh and disable.sh scripts, ensures minimised downtime during PodNet failure.